Stord Expands SOC 2 Type II Compliance, Strengthening Customer Trust and Data Security
Stord
AUGUST 17, 2023
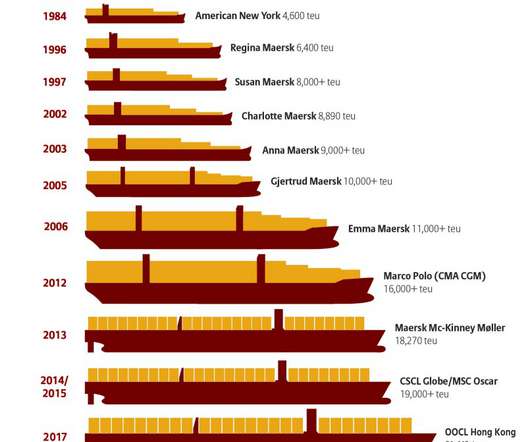
This report successfully validates Stord’s policies and procedures through an independent third-party assessment, demonstrating Stord’s continued commitment to upholding the most rigorous security standards and protecting its customers' data. With SOC 2 compliance, Stord can enable faster and more efficient sales engagements.













































Let's personalize your content