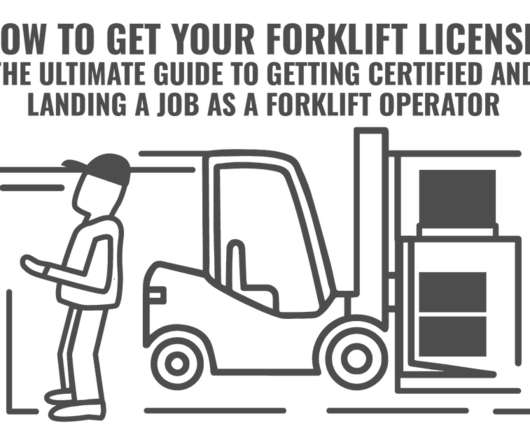
How to Protect Your Customers & Brand from Ecommerce Fraud
Ship Monk
APRIL 16, 2024
To be clear, the blame lies with the hackers and criminals, but if a data breach or you approve an unauthorized transaction, the customer is going to blame your business. Know the Warning Signs If you know what to look for and have the technology to collect and examine the data, there are several red flags that may indicate ecommerce fraud.

















Let's personalize your content