Transloading: A Comprehensive Guide With Client Examples
Dedola Global Logistics
JANUARY 14, 2023
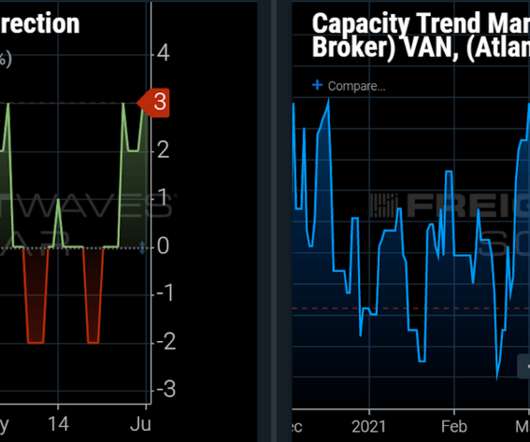
Transloading: A Comprehensive Guide With Client Examples . For example, a shipment of heavy machinery may be transferred from a cargo ship to a truck using a break-bulk method, with the machinery being stored temporarily in a warehouse before being loaded onto the truck for the final leg of the journey. DID YOU READ IT? Contact Us.










































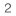

Let's personalize your content